Building on the Wireguard protocol Tailscale enables something truly extraordinary: effortless GAN Global Area Networking point-to-point across firewalls and routers on any network.
No firewall configuration, no fiddling with port forwarding, no bandwidth limits, no external VPN server and no digging through thousands of lines of log files. No configuration files.
This is serious black magic - for the details see NAT Traversal and ICE Interactive Connectivity Establishment.
Build your personal Tailnet by adding servers, workstations and mobile phones. Install the Tailscale client and authenticate with Google, GitHub, Microsoft, or e-mail credentials.
Tailscale is free for up to three users on the same Tailnet and 100 devices.
All devices are authenticated on your Tailnet, there is no need for private-public keys when starting a SSH session or transferring files with SSHFS, the Tailscale client provides a SSH server for connecting to remote devices.
All hosts are assigned a Tailnet IP-address 100.x.x.x which does not change. Magic DNS enables connections using the host name, a SSH session using Tailscale SSH and Magic DNS becomes....
ssh user@hostname
Accessing web servers
Web services can be made publicly available, or restricted to your Tailnet. The tailscale serve command exposes the service on a sub-domain under ts.net such as dolphin-coffee.ts.net with automatic SSL-certificate, making the host available like this...
https://media.dolphin-coffee.ts.net
The Coordination server
A Tailnet is created by the Tailscale Coordination Server. The client sends its public key, receives a list of hosts on the private Tailnet with their public keys. Now you have a secure global network point-to-point using the Wireguard protocol, tunneling through firewalls and routers.
The private key never leaves its node, and should the Coordination server go down the connections stay up, connections are point-to-point. When a direct connection can not be established Tailscale provides a relay to bypass firewalls and routers.
Use cases
Connect a host over x2go to share desktops, files, applications, printers and audio - globally.
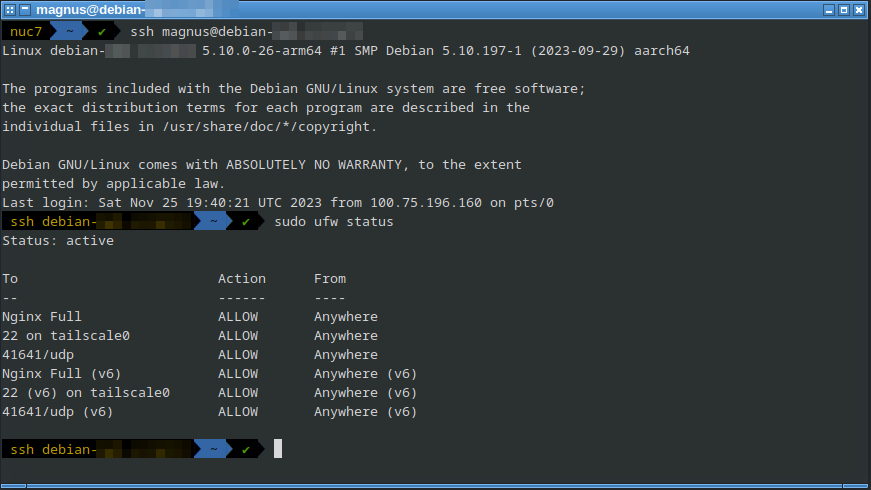
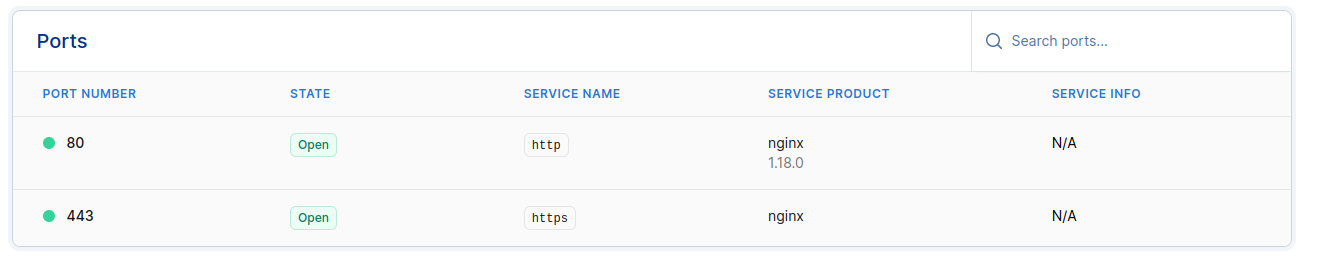
Secure a cloud server with Tailscale by restricting SSH access to Tailscale's network interface, this makes the server invisible to hackers. Configure the UFW firewall with sudo ufw allow in on tailscale0 to any port 22 and it is done. Tailscale has written a detailed guide - only port 80 and 443 will be visible from the internet-side.
All this without editing a single configuration file or any changes to firewall or routers.